Email: anwenqq2690502116@gmail.com
RFID Security Research - RFID Card Devices
Radio Frequency Identification (RFID) is the abbreviation of Radio Frequency Identification. The principle is to conduct non-contact data communication between the reader and the tag to achieve the purpose of identifying the target.
RFID is widely used, typical applications include access control, parking lot control, and material management.
Card device
Various access control cards, water cards, etc. encountered in life, various functions are realized by chips and coils packaged in the card, and these chips have different frequencies, capacities, and read and write performance. Common card types include IC cards and ID cards, and there is also a UID card.
No. 2 ID key chain - access control and attendance induction card - property authorization 125KHZ card - community access RFID card
The full name of the ID card is an identification card, which is a non-writable induction card with a fixed number. The frequency is 125KHz, which belongs to low frequency. Generally used for access control. The ID card cannot write data, and its recorded content can only be written once by the chip manufacturer, and only the card number can be read out for use.
For example, the common white card is one-time write data, the cheap amiibo card for switch.
The full name of IC card is integrated circuit card, also known as smart card. Readable and writable, large capacity, encryption function, safe and reliable data recording, more convenient to use, belongs to high frequency, frequency is 135MHz, mainly used in card system, consumer system, etc.
RFID device card - ID cards - RFID Security Research - RFID Card Devices
The security of IC card is far greater than that of ID card. The card number in the ID card is read without any authority and is easy to imitate. The reading and writing of data recorded in the IC card requires corresponding password authentication, and even each area in the card has different password protection to fully protect data security
UID card is a kind of IC card. UID card can modify any sector. As the sub-card of M1 copy, it is mainly used in IC card copy. The card is fully compatible with mifare 1k card. The block0 of the card (the block where the UID is located) can be modified arbitrarily and repeatedly.

Hotel IC Card - White Card ID Card - M1 Proximity Card Smart Access Control Card - Hotel T5577 Card
For ordinary IC cards, sector 0 cannot be modified, and other sectors can be repeatedly erased and written. The smart card issuers such as elevator cards and access control cards we use all use M1 cards, which can be understood as the original cards issued by the property.
UID cards are divided into:
FUID: anti-shielding one-time erase 0 sector 0 block.
Ufuid: Anti-shielding and repeated erasing of 0 sectors and 0 blocks, after locking the card, no more erasing of 0 sectors and 0 blocks.
Cuid: Anti-screen rewritable 0 sector 0 blocks (requires special equipment and software to be rewritable)
CUID is a more advanced firewall card than UID.
 ID cards - RFID IOT CRAD - IoT RFID Card
ID cards - RFID IOT CRAD - IoT RFID Card
In some communities, the card reader has a firewall, and the card copied by the ordinary duplicator cannot be used once or even once, so the firewall version must be used.
Read/write card/decrypt card device
The ID card needs to read and write data through the device software.
The data of the mifare series IC card can be read and written through the mobile phone software MCT (mifare classic tool).
Card decryption
For an encrypted IC card, if you want to read the data in the card, you first need to obtain the KEYA or KEYB of all sectors. Generally, the keys are kept secret. When we only have the card, the decryption needs to be supported by hardware. , such as pn532, acr122u, proxmark3, etc.
PM3 (Proxmark3)
Proxmark3 is an open-source hardware designed and developed by Jonathan Westhues. It mainly uses RFID sniffing, reading and cloning operations. Proxmark3 has a powerful function for IC card decryption and has many ways to exploit vulnerabilities.
Price: ranging from 200-300 yuan
Advantages: the best performance, strong decryption ability.
Disadvantages: There is a certain threshold for use, and the price is slightly expensive.
Purchase contact WhatsApp:+8618062443671
There are many domestic pm3s available on tb. In addition to the imitation of the original version, there are also some with added original functions. You can choose by yourself.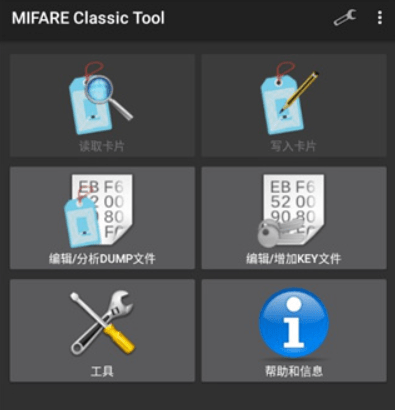
mifare tool windows download - mifare tools android - MIFARE CLASSIC TOOL
You can also buy materials and DIY according to your needs
PN532
Price: around 40 yuan (with TTL to USB)
Advantages: cheap price, good decryption ability
Disadvantages: The speed is slow, you need to connect the TTL line yourself, the stability is average.
Protocol supports more types of PN than RC series. PN supports NFC protocol, and RC mainly supports ISO14443A/B.
PN532 supports limited card types. M1T has appeared in recent years. It is a very useful open source program that supports multiple decryption methods. But limited to hardware performance, the decryption speed is not as good as Proxmark3, but the decryption ability is not inferior to Proxmark3 in general scenarios.
iCopy3
Advantages: easy to use, more types of decryption.
Disadvantages: the price is ridiculously high, and the method of use is single
The iCopy3 device is mainly for locksmiths, and I personally do not recommend buying it. Especially when it comes to data modification and data analysis in the later stage, it is not as convenient as Proxmark3 and PN532. iCopy is mainly suitable for operating scenarios where the computer cannot be carried outdoors
RC-522
Price: about 10 yuan
Advantages: cheap
Disadvantages: does not support writing card, can only read IC card