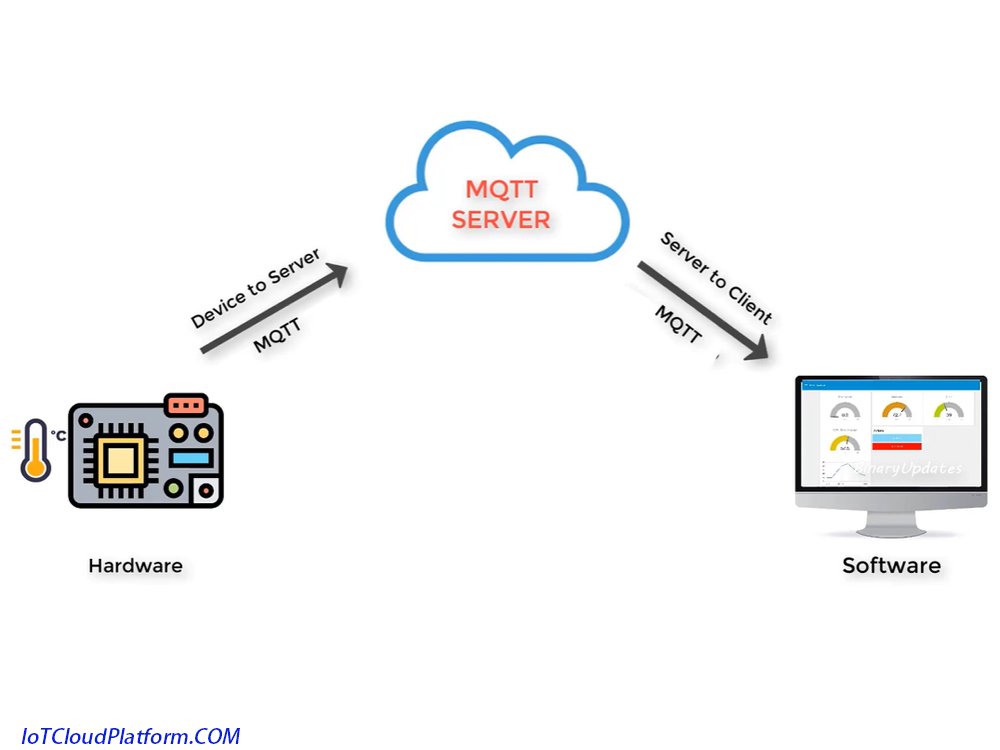
Explaining the MQTT Protocol Technology in the Internet of Things
MQTT (MESSAGE QUEUING Telemetry Transport) protocol technology in the Internet of Things (IoT) is a lightweight message transmission protocol based on the release/subscription mode.
It is especially suitable for the IoT of the Internet of Things with limited network bandwidth, equipment computing resources and storage resources. Scene.
The following is a detailed introduction to the MQTT protocol technology of the Internet of Things cloud platform.
MQTT protocol overview
The MQTT protocol was built on the TCP/IP protocol and was released by IBM in 1999. It is now an OASIS standard message transmission protocol for the Internet of Things (IoT).
The biggest advantage of MQTT is to provide real -time and reliable message services for connecting remote devices with very small code and limited bandwidth. The MQTT protocol is lightweight, simple, open and easy to achieve, which makes them have a wide range of applications in the Internet of Things, small devices, and mobile applications.
MQTT protocol is used in the Internet of Things industry
MQTT Agreement’s core feature
1. Lightweight and efficient:
The amount of code of the MQTT client is very small and the demand for system resources is also low, so it is very suitable for use on small micro -controllers. In addition, the head field of the MQTT message is small, which optimizes the network bandwidth and further improves the transmission efficiency.
2. Support two -way communication:
The MQTT protocol supports message transmission between the device to the cloud and the cloud to the device. This makes the broadcast message of a large amount of equipment relatively simple.
3. scalability:
The MQTT protocol can expand to connect millions of IoT devices to meet the needs of large -scale equipment deployment and data collection.
4. Reliable messages pass:
The MQTT agreement provides three definition service quality levels for this: up to once (QOS 0), at least once (QOS 1), and just once (QOS 2) to meet the needs of different scenarios to pass the reliability of messages.
5. Support the unreliable network:
Many IoT devices are connected through mobile honeycomb networks, and this network environment is usually unstable. However, the MQTT protocol has reduced the time and communication latency between clients and agents through the design of long -term sessions, thereby providing more reliable message transmission in unreliable network environments.
6. Security:
The MQTT protocol can easily use the TLS (transport layer security protocol) to encrypt the transmission messages, and supports modern identity verification protocols such as OAUTH to verify the client to ensure the security of the message transmission and the legitimacy of the client identity.
Mqtt Agreement Core component and role
In the MQTT protocol, the following core components and roles are mainly involved:
1. MQTT BROKER (Message Agent):
MQTT Broker is the message middleware. It is responsible for receiving messages sent by the publisher and forwarding the message to the subscriber according to the subscriber subscription theme. It manages client connection, processing subscriptions and recounting, and guarantees to send messages according to the designated service quality (QOS) level.
2. mqtt client (client):
MQTT Client refers to a device running MQTT library and connecting to MQTT BROKER through the network. These devices can be a microcontroller or a mature server. It implements the client of the MQTT protocol, which can be publishers, subscribers, or both.
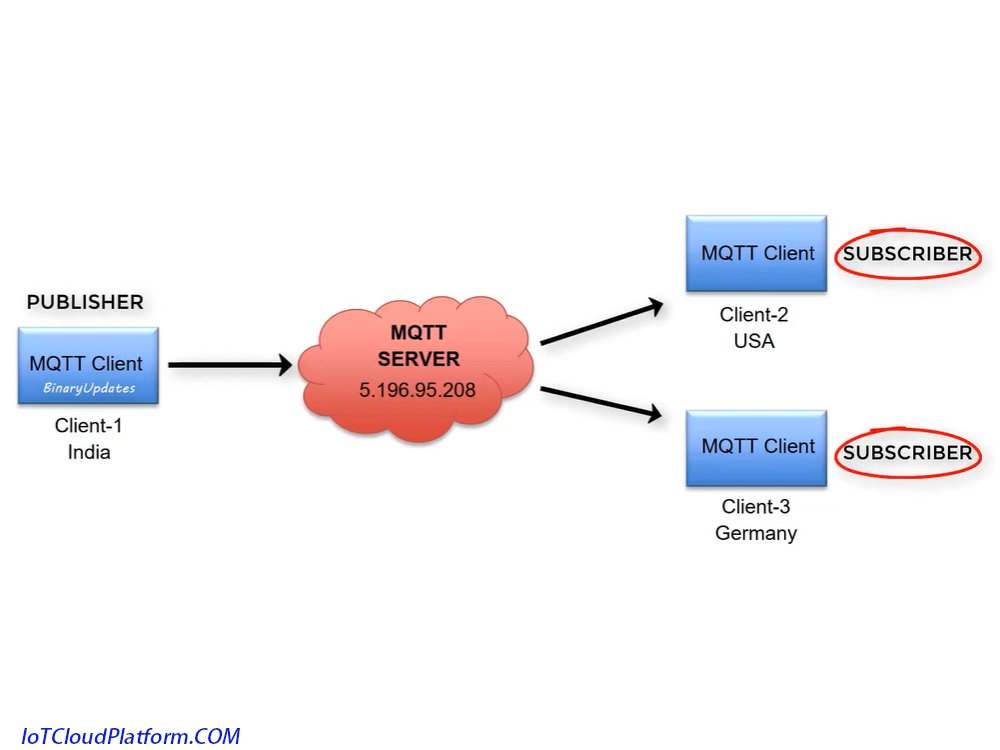
In the release/subscription mode, there are the following main characters:
- Publisher (Publisher) : Responsible for publishing news.
- Subscriber: Responsible for subscribing to the topic of interest and receiving news from the publisher.
mqtt protocol message transmission mechanism
The MQTT protocol uses the release/subscription model for message transmission. This model is proven to be very effective in the IoT (IoT) scenarios. The following is a detailed explanation of the MQTT protocol message transmission mechanism:
release/subscription model
The MQTT protocol is transmitted based on the release/subscription model. In this model, there are two key roles: publishers and subscribers. Publisher is responsible for publishing the message to a specific topic, and the subscriber to receive the message by subscribing these themes. As a central node (Broker), it is responsible for receiving, storing, routes, and reposting messages.
Message transfer process
- Post message:
- Publisher publishes the message to the specified theme.
- After receiving the message, the message agent will be stored in the internal line.
- Subscribe to the topic:
- Subscriber sends a subscription request to the message agent to specify the topic to be subscribed.
- After receiving the subscription request, the message agent will add the subscriber to the subscriber list of the corresponding theme.
- message pass:
- When the message is released to a certain theme, the message agency will push the message to all subscribers who subscribe to the theme.
- After receiving the message, the subscriber can process it as needed.
Service Quality (QOS) level
The MQTT protocol supports three service quality (QOS) levels to ensure the transmission reliability of the message in the network:
Qos 0: Most of the time
- At this level, the message is sent once without retry or confirmation.
- Applicable to application scenarios that require low reliability, such as real -time updates of sensor data.
Qos 1: At least once
- In this level, the news is sent at least once and ensures at least once.
- The sender will wait for the recipient’s confirmation. If the confirmation is not received, the message will be retrieved.
- Applicable to the scene that needs to be processed at least once, such as control instructions.
Qos 2: Only once
- In this level, the message is sent and ensured only once.
- The sender and the receiver use four handshake to ensure that the message is sent only once.
- Applicable to scenes that need to ensure that the news is not repeated, such as financial transactions.
long -lasting session and message retention
long -lasting session:
- MQTT supports a long -lasting session mechanism. If the client is re -connected after the connection is disconnected, the message agency will save the client’s subscription information and unsatisfactory messages.
- In this way, the client can receive the news that it is not received during the disconnect.
message reserves:
- When the message is released, the sender can set the “reservation” logo.
- This means that the message should be retained on the message agency. When a new client subscribes to the theme, the message agency will send the message to the new subscriber.
- This ensures the latest news that new subscribers can receive the theme and avoid missing the news because of disconnection.
Security of MQTT protocol
Security is an important aspect that cannot be ignored in IoT applications, and the MQTT protocol was designed with this in mind. However, the original MQTT 3.1.1 version has some deficiencies in security, such as the default use of insecure TCP connections and the lack of built-in authentication and authorization mechanisms. To address these issues, MQTT 5.0 introduces more powerful security features, including:
1. TLS/SSL encryption:
MQTT 5.0 supports the use of TLS/SSL to encrypt connections, ensuring the confidentiality and integrity of data during transmission.
2. Client authentication:
MQTT 5.0 supports client authentication through mechanisms such as TLS/SSL client certificates, username/password, and OAuth 2.0, ensuring that only legitimate clients can connect to the MQTT Broker.
3. Authorization control:
MQTT 5.0 introduces a more fine-grained authorization control mechanism, allowing the Broker to control the permissions of the client’s operations based on information such as the client’s identity and topic.
4. Message encryption:
Although the MQTT protocol itself does not directly encrypt the message content, it can encrypt the message by using encryption algorithms at the application layer, and then transmit the encrypted message through MQTT.
5. Session security:
MQTT 5.0 supports persistent sessions, but the use of persistent sessions can be restricted through configuration to reduce potential security risks. At the same time, Broker can regularly clean up expired sessions and subscription information to reduce the attack surface.
6. Security auditing and monitoring:
MQTT Broker can record client connection, disconnection, publishing, subscription and other operation logs, and perform security auditing and monitoring. This helps to detect and respond to potential security threats in a timely manner.
Although MQTT 5.0 has made significant improvements in security, the following points should still be noted in actual applications:
- Make sure to use the latest version of the MQTT protocol and library to obtain the latest security features and fix known security vulnerabilities.
- Enable TLS/SSL encryption and configure strong passwords and certificate policies.
- Implement strict authentication and authorization control mechanisms to ensure that only legitimate clients can access and operate MQTT Broker.
- Encrypt sensitive information to avoid leakage during transmission.
- Regularly conduct security audits and monitoring of MQTT Broker to promptly detect and respond to potential security threats.
Future development and innovation of MQTT protocol
With the continuous advancement of IoT technology and the continuous expansion of application scenarios, the MQTT protocol is also constantly developing and innovating. Here are some prospects for the future development trend of the MQTT protocol:
1. Enhanced security:
- More advanced encryption technology: With the development of technologies such as quantum computing, existing encryption technologies may face challenges. Therefore, the MQTT protocol may introduce more advanced encryption technologies, such as quantum encryption, to ensure the security of data transmission.
- Zero trust security model: In the future, the MQTT protocol may draw on the zero trust security model, that is, no network traffic is trusted by default, but each request is authenticated and authorized.
2. Optimize performance:
- More efficient message transmission: In order to reduce network latency and improve message transmission efficiency, the MQTT protocol may further optimize its message format and transmission mechanism.
- Support large-scale device connection: With the continuous increase of IoT devices, the MQTT protocol needs to be able to support larger-scale device connections and concurrent processing.
3. Enhance scalability:
- Plug-in architecture: The MQTT protocol may adopt a plug-in architecture, allowing developers to add or remove functions as needed, thereby enhancing the scalability of the protocol.
- Integration with other protocols: In order to support more diverse application scenarios, the MQTT protocol may be integrated with other IoT protocols (such as CoAP, HTTP/2, WebSocket, etc.) to achieve interoperability between protocols.
4. Intelligent management:
- Automatic configuration and monitoring: In the future, the MQTT protocol may introduce automated configuration and monitoring functions to simplify device management and maintenance.
- Intelligent routing and load balancing: In order to optimize the utilization of network resources, the MQTT protocol may implement more intelligent routing and load balancing mechanisms.
5. Support edge computing:
- Edge node processing: With the rise of edge computing, the MQTT protocol may support data processing and analysis at edge nodes to reduce dependence on cloud resources.
- Distributed architecture: In order to support edge computing scenarios, the MQTT protocol may adopt a distributed architecture to achieve message delivery across edge nodes and the cloud.
6. Standardization and compliance:
- International standardization: The MQTT protocol may further promote its international standardization process to ensure that IoT devices in different countries and regions can connect and communicate seamlessly.
- Compliance requirements: With the increasing popularity of IoT applications, the MQTT protocol may need to meet more compliance requirements, such as data protection regulations, network security standards, etc.
Optimization strategies for MQTT protocol in specific scenarios
In different application scenarios, the MQTT protocol may need to adopt different optimization strategies to meet specific needs. The following are some optimization strategies for common scenarios:
1. Low bandwidth environment:
- Compress message content: In a bandwidth-constrained environment, a compression algorithm can be used to compress the message content to reduce the amount of data transmitted.
- Reduce message frequency: By adjusting the frequency of message publishing, the network bandwidth usage can be reduced.
2. High latency environment:
- Increase QoS level: In a high latency environment, a higher QoS level can be used to ensure reliable message transmission.
- Use persistent session: The persistent session mechanism can maintain the connection status between the client and the Broker when the network is unstable.
3. Large-scale device connection:
- Distributed Broker architecture: The distributed Broker architecture can disperse the pressure of device connection and message processing and improve the scalability of the system.
- Device group management: Through device group management, the management and maintenance of a large number of devices can be simplified.
4. Scenarios with high security requirements:
- Use TLS/SSL encryption: In scenarios with high security requirements, TLS/SSL should be used to encrypt MQTT connections.
- Implement strict authentication and authorization: By implementing strict authentication and authorization mechanisms, it can be ensured that only legitimate devices can connect to the MQTT Broker and publish or subscribe to messages.
5. Resource-constrained devices:
- Use lightweight client libraries: On resource-constrained devices, lightweight MQTT client libraries should be used to reduce resource consumption.
- Optimize message formats: By optimizing the message format, you can reduce the resource usage of the device when processing messages.
Summary
As a lightweight IoT message transmission protocol, the MQTT protocol has broad application prospects and huge development potential in the field of IoT. Through an in-depth understanding of its core features, core components, message delivery mechanisms, topics and wildcards, and service quality levels, we can better grasp the working principles and application value of the MQTT protocol.
In the future, with the continuous advancement of IoT technology and the continuous expansion of application scenarios, the MQTT protocol will continue to develop and innovate. Through efforts in enhancing security, optimizing performance, enhancing scalability, intelligent management, supporting edge computing, and promoting standardization and compliance, the MQTT protocol will be able to better adapt to the development needs of the IoT field.
At the same time, in different application scenarios, the MQTT protocol also needs to adopt different optimization strategies to meet specific needs. By compressing message content, reducing message frequency, increasing QoS level, using persistent sessions, distributed broker architecture, device group management, using TLS/SSL encryption, implementing strict authentication and authorization, and using lightweight client libraries, we can further improve the performance and security of the MQTT protocol in IoT applications.
In short, as one of the important communication protocols in the field of IoT, the MQTT protocol will continue to play its unique role and value and make greater contributions to the development of IoT.
About IoT Cloud Platform
IOT Cloud Platform (blog.iotcloudplatform.com) focuses on IoT design, IoT programming, security IoT, industrial IoT, military IoT, best IoT projects, IoT creativity, IoT companies, Chinese IoT companies, American IoT companies, top IoT companies, IoT modules, embedded development, IoT circuit boards, IoT solutions, Raspberry Pi development and design, Arduino programming, programming languages, RFID, lora devices, IoT systems, sensors, temperature and humidity sensors, liquid level sensors, sensor devices, artificial intelligence, blockchain, robotic arms, smart homes, smart cities, smart agricultural factories, edge computing, big data, cloud computing, brain-computer interfaces, machine learning, robots, VR/AR, AI simulation technology, motion control, new energy, photovoltaic solar energy, lithium batteries, silicon brain SBB, unmanned aerospace navigation, unmanned driving, AGI, chips, semiconductors, smart hardware and other scientific and technological knowledge.
FAQs
The following are questions and answers about the MQTT protocol:
MQTT (Message Queuing Telemetry Transport) is a TCP/IP-based, extremely simple and lightweight message protocol based on the publish-subscribe model designed for hardware resource and bandwidth-constrained, high-latency, and unreliable network scenarios.
The main features of the MQTT protocol include openness and simplicity, publish/subscribe model, load transparency, reliable connection based on TCP/IP, message quality of service (QoS) support, and low transmission overhead.
The MQTT protocol provides three QoS levels, namely QoS 0 (at most once), QoS 1 (at least once), and QoS 2 (only once). These levels meet different reliability requirements.
The MQTT message structure consists of three parts: fixed header, variable header, and payload. The fixed header contains basic information about the message, such as the message type and control flags; the variable header contains additional metadata; and the payload stores the actual data content transmitted.
The MQTT protocol implements the publish/subscribe model through topics and subscribers. Publishers publish messages to specific topics, and subscribers subscribe to these topics to receive related messages.
The MQTT protocol has been widely used in the field of the Internet of Things. Its lightweight, reliability, and flexibility make it an ideal choice for embedded device information transmission. Sensors, smart home devices, industrial control equipment, etc. can all use the MQTT protocol for communication and data transmission.
The MQTT DISCONNECT message is a control message used to inform the MQTT server that the client wants to disconnect and no longer receive or send any messages. This helps ensure the correctness of the protocol and the correct release of resources.
When selecting the QoS level, you need to balance the reliability and transmission delay of the message according to the specific application scenario. Critical data such as commands and alarm information should use a higher QoS (such as QoS 2), while real-time but non-critical data can use a lower QoS (such as QoS 0 or QoS 1).
The MQTT protocol itself does not provide a mandatory encryption mechanism, but the security of data transmission can be protected by using TLS/SSL encryption. In addition, certificate-based or OAuth-based authentication mechanisms can be implemented to enhance the security authentication of devices and users.
The MQTT protocol ensures the stable transmission of messages by providing three QoS levels, using TCP/IP reliable connections, implementing disconnection reconnection mechanisms, and reasonably configuring message retention policies. These mechanisms work together to enable the MQTT protocol to maintain high message transmission reliability even in unstable network environments.
IOT Cloud Platform
IOT Cloud Platform is an IoT portal established by a Chinese IoT company, focusing on technical solutions in the fields of agricultural IoT, industrial IoT, medical IoT, security IoT, military IoT, meteorological IoT, consumer IoT, automotive IoT, commercial IoT, infrastructure IoT, smart warehousing and logistics, smart home, smart city, smart healthcare, smart lighting, etc.
The IoT Cloud Platform blog is a top IoT technology stack, providing technical knowledge on IoT, robotics, artificial intelligence (generative artificial intelligence AIGC), edge computing, AR/VR, cloud computing, quantum computing, blockchain, smart surveillance cameras, drones, RFID tags, gateways, GPS, 3D printing, 4D printing, autonomous driving, etc.



